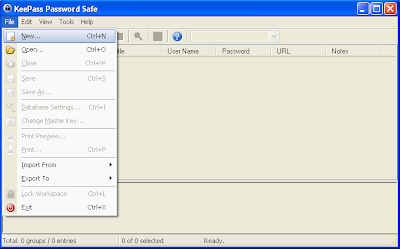
First..... go to www.truecrypt.org to get your TrueCrypt program.......(If the URL does not work... go to any search engines and search for "TrueCrypt")
Click on the Downloads button and then under the Windows Vista/XP/2000 section..... click on the Downloads button again to download the TrueCrypt program~~~ After successfully downloading the file, run the installer and proceed with deafult options.......
When the installation completes launch the Truecrypt program and select NO if they prompt you for a tutorial......(Don't waste your time)
Now.... Your TrueCrypt window should be the same as what is shown in the following screenshot.....
 To start off... click on the Create Volume button........The Creation Wizard window should appear as shown in the next screenshot.......
To start off... click on the Create Volume button........The Creation Wizard window should appear as shown in the next screenshot....... Here, choose the first option Create an encrypted file container and click Next to proceed on....Keep on following any default options until you have reach a window prompting you for the volume size as shown in the screenshot below....
Here, choose the first option Create an encrypted file container and click Next to proceed on....Keep on following any default options until you have reach a window prompting you for the volume size as shown in the screenshot below.... The volume size is recommended to be at 1MB as this is just a testing....Remember that the MB option is selected and not the others.....now click Next and yet again proceed on with default options...........
The volume size is recommended to be at 1MB as this is just a testing....Remember that the MB option is selected and not the others.....now click Next and yet again proceed on with default options........... When you have reach the window on "Volume Format" as shown in the screenshot above....move your mouse around, within the window, for at least 30 seconds to strengthen the encryption...(I do not kknow why, but just do it....If you notice, when you move your cursor around,,, the line of letters and numbers in Random Pool: begins to change every fast as compared to when your don't move your cursor)
When you have reach the window on "Volume Format" as shown in the screenshot above....move your mouse around, within the window, for at least 30 seconds to strengthen the encryption...(I do not kknow why, but just do it....If you notice, when you move your cursor around,,, the line of letters and numbers in Random Pool: begins to change every fast as compared to when your don't move your cursor)After moving your cursor around for at least 30 seconds or until you are satisfied..... click Next to complete your volume creation.....
 When you have finish creating your volume you should be back at the home window of truecrypt....But now you should see that one of your drives is not empty anymore as indicated in the screenshot above by the red rectangle^^^^^
When you have finish creating your volume you should be back at the home window of truecrypt....But now you should see that one of your drives is not empty anymore as indicated in the screenshot above by the red rectangle^^^^^Now with a drive activated.... Remember the Encryted.docx & Not Encrypted.docx from the previous post????? now you can move the Encrypted.docx into the activated drive, which you can find when you open My Computer....... Now try opening both Encrypted.docx & Not Encrypted.docx did you noticee any difference in the time taken to open these 2 files????
After you are done,, to unactivate your encrypted drive, go back to your TrueCrypt program and simply click on the Dismount button......
There you have it :)